Notes on Azure Fundamentals AZ-900 Certificate
Get your first Azure Certificate after reading these notes
Table of contents
- Introduction
- Notes
- What is the Azure free account?
- What are public, private, and hybrid cloud models?
- Cloud model comparison
- What are cloud service models?
- Azure regions, availability zones, and region pairs
- Azure regions
- Azure resources
- Azure Resource Manager
- Hierarchy of management groups and subscriptions
- What's Azure Security Center?
- Detect and respond to security threats by using Azure Sentinel
- Store and manage secrets by using Azure Key Vault
- What are the benefits of Azure Key Vault?
- Azure Dedicated Host:
- Layers of defense in depth :
- Security posture
- What's Azure Firewall?
- What are network security groups?
- Compare authentication and authorization
- Azure Role-Based Access Control :- Azure RBAC
- Plan and manage your Azure costs
- Total Cost of Ownership Calculator= TCO
- What types of Azure subscriptions can I use?
- How do I purchase Azure services?
- What factors affect cost?
Introduction
It's 2022 & cloud computing is at its peak. You can be a web developer, or a Site Reliability Engineer or Data Scientist, knowledge & experience on cloud can help you grow on your journey.
Azure being one of the leading Cloud Service Provider, getting yourself certified would boost your career & open a lot of doors for you. Here is the note that helped me prepare for my exam & it saved hours of my time to go through tons of videos.
All you need for AZ-900: Microsoft Azure Fundamentals Certification
Notes
What is the Azure free account?
The Azure free account includes:
- Free access to popular Azure products for 12 months.
- A credit to spend for the first 30 days.
- Access to more than 25 products that are always free.
What are public, private, and hybrid cloud models?
Public cloud
- Services are offered over the public internet
- Available to anyone who wants to purchase them
- Cloud resources, are owned and operated by a third-party
Private cloud
- exclusively by users from one business or organization.
- A private cloud can be physically located at your organization's on-site (on-premises) datacenter, or it can be hosted by a third-party service provider.
Hybrid cloud
A hybrid cloud is a computing environment that combines a public cloud and a private cloud by allowing data and applications to be shared between them.
Cloud model comparison
Public cloud
- No capital expenditures to scale up.
- Applications can be quickly provisioned and deprovisioned.
- Organizations pay only for what they use.
Private cloud
- Hardware must be purchased for start-up and maintenance.
- Organizations have complete control over resources and security.
- Organizations are responsible for hardware maintenance and updates.
Hybrid cloud
- Provides the most flexibility.
- Organizations determine where to run their applications.
- Organizations control security, compliance, or legal requirements.
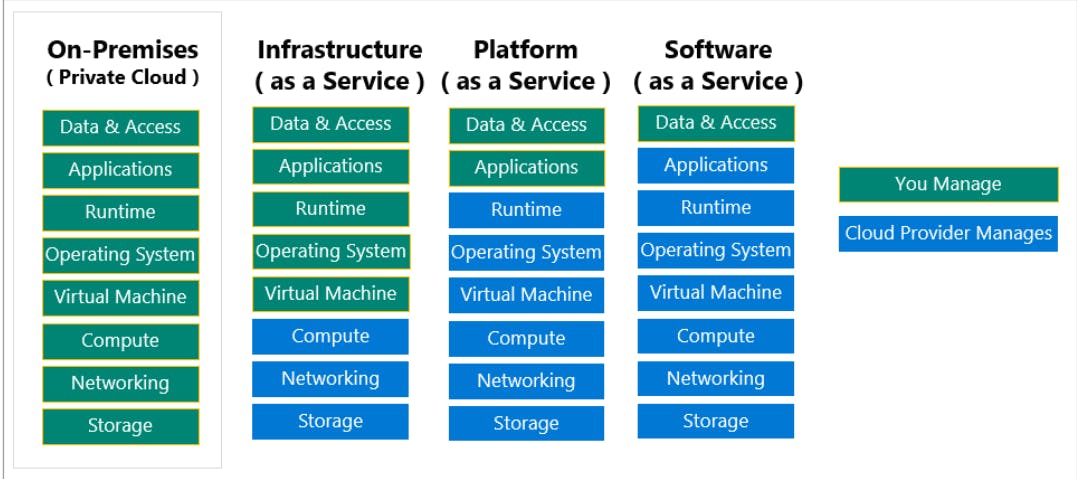
What are cloud service models?
Infrastructure-as-a-Service :- virtual machine
Platform-as-a-Service :-Azure App Services provides a managed hosting environment
Software-as-a-Service :- Microsoft Office 365 provides a fully working version of Microsoft Office
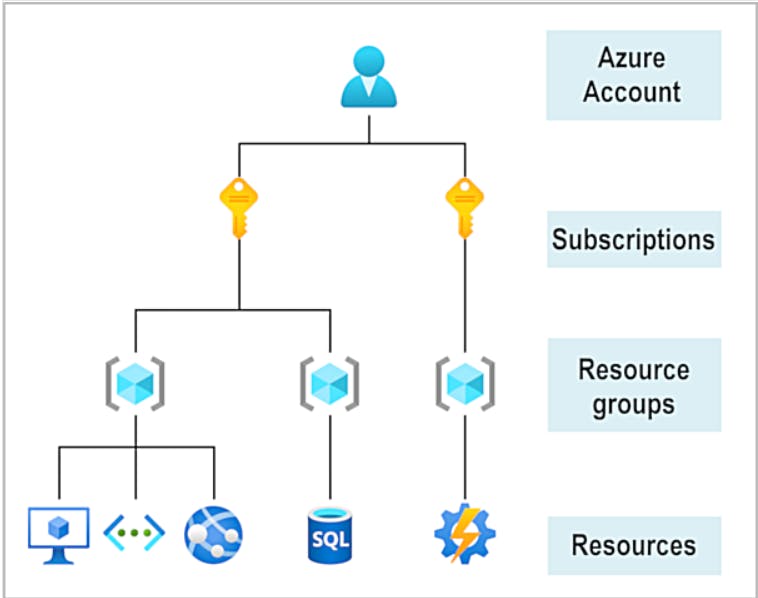
- Subscriptions: A subscription groups together user accounts and the resources that have been created by those user accounts. For each subscription, there are limits or quotas on the amount of resources that you can create and use. Organizations can use subscriptions to manage costs and (Access control boundary:) the resources that are created by users, teams, or projects.
- Management groups: These groups help you manage access, policy, and compliance for multiple subscriptions. All subscriptions in a management group automatically inherit the conditions applied to the management group.
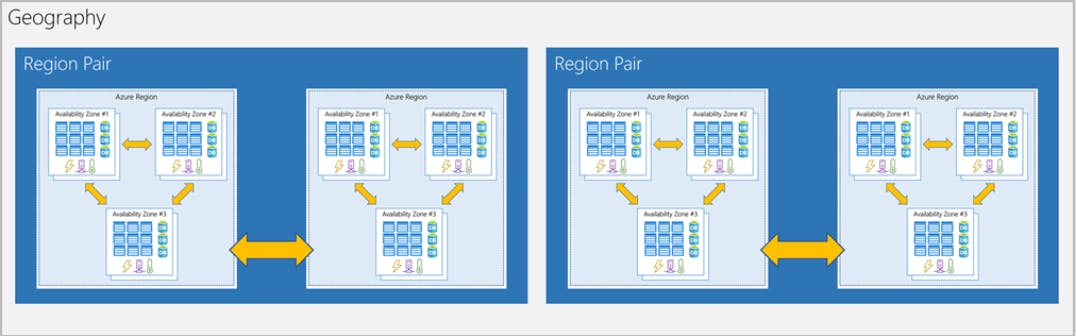
Azure regions, availability zones, and region pairs
Azure regions
A region is a geographical area on the planet that contains at least one but potentially multiple datacenters that are nearby and networked together with a low-latency network
There are also some global Azure services that don't require you to select a particular region, such as Azure Active Directory, Azure Traffic Manager, and Azure DNS.
Azure availability zones : There's a minimum of three zones within a single region.
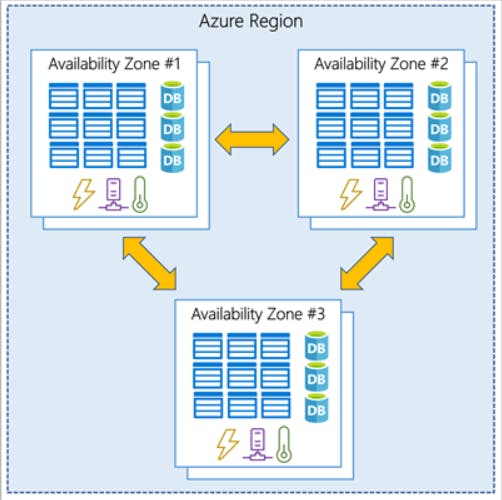
Azure region pairs : Each Azure region is always paired with another region within the same geography (such as US, Europe, or Asia) at least 300 miles away.
Azure resources
- All resources must be in a resource group, and a resource can only be a member of a single resource group.
- Resource groups can't be nested.
- Before any resource can be provisioned, you need a resource group for it to be placed in.
- Resource groups are also a scope for applying role-based access control (RBAC) permissions.
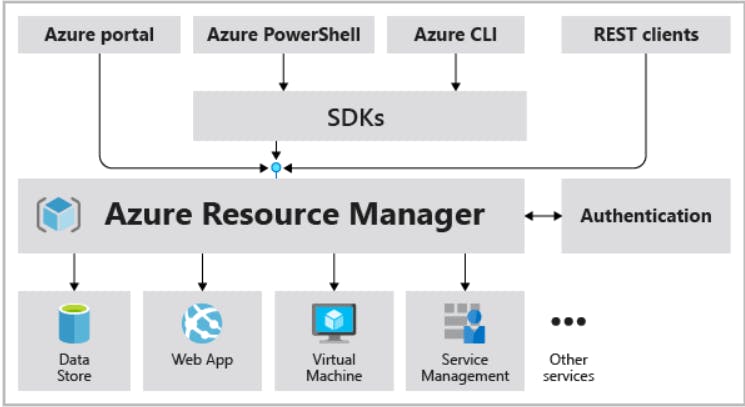
Azure Resource Manager
- Azure Resource Manager is the deployment and management service for Azure.
- It provides a management layer that enables you to create, update, and delete resources in your Azure account.
- You use management features like access control, locks, and tags to secure and organize your resources after deployment.
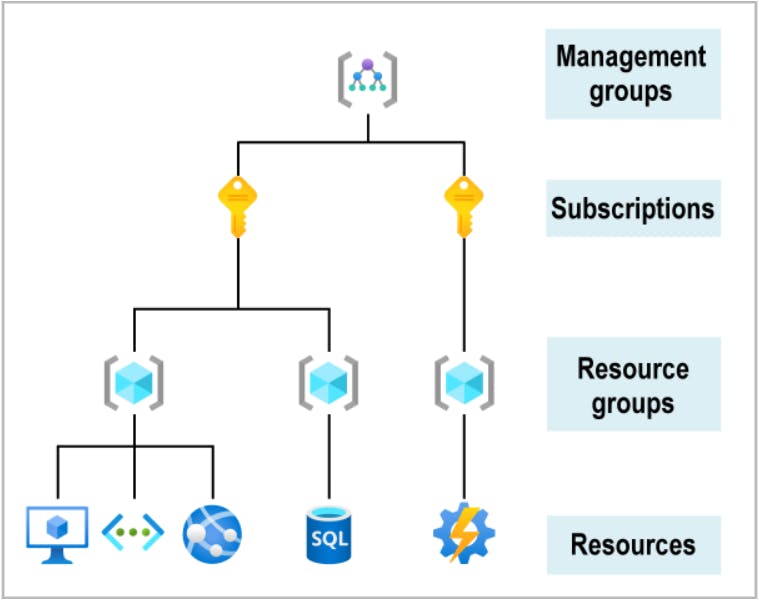
Hierarchy of management groups and subscriptions
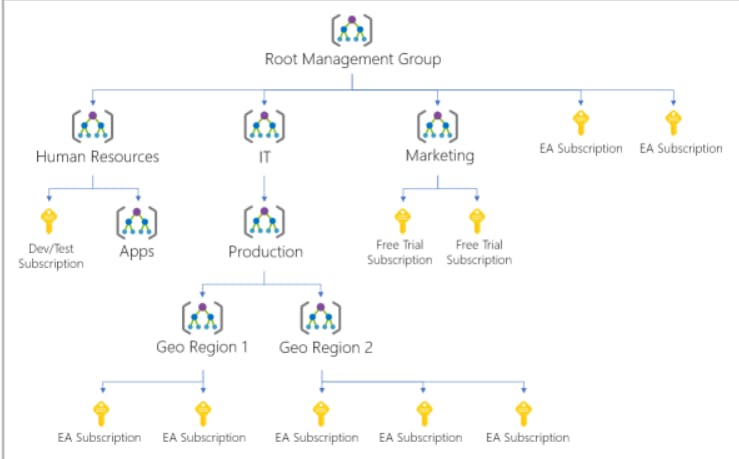
- 10,000 management groups can be supported in a single directory.
- A management group tree can support up to six levels of depth. This limit doesn't include the root level or the subscription level.
- Each management group and subscription can support only one parent.
- Each management group can have many children.
- All subscriptions and management groups are within a single hierarchy in each directory.
What's Azure Security Center?
Azure Security Center is a monitoring service verify security posture
- Monitor security settings across on-premises and cloud workloads.
- Automatically apply required security settings to new resources as they come online.
- Provide security recommendations that are based on your current configurations, resources, and networks.
- Continuously monitor your resources and perform automatic security assessments to identify potential vulnerabilities before those vulnerabilities can be exploited.
- Use machine learning to detect and block malware from being installed on your virtual machines (VMs) and other resources. You can also use adaptive application controls to define rules that list allowed applications to ensure that only applications you allow can run.
- Detect and analyze potential inbound attacks and investigate threats and any post-breach activity that might have occurred.
- Provide just-in-time access control for network ports. Doing so reduces your attack surface by ensuring that the network only allows traffic that you require at the time that you need it to.
Secure score is a measurement of an organization's security posture. (100%=60 points)
In the Resource security hygiene section, Tailwind Traders can see the health of its resources from a security perspective.
Security Center includes advanced cloud defense capabilities
- Just-in-time VM access This access blocks traffic by default to specific network ports of VMs, but allows traffic for a specified time when an admin requests and approves it.
- Adaptive application controls control which applications are allowed to run on its VMs. In the background, Security Center uses machine learning to look at the processes running on a VM. It creates exception rules for each resource group that holds the VMs and provides recommendations. This process provides alerts that inform the company about unauthorized applications that are running on its VMs.
- Adaptive network hardening Security Center can monitor the internet traffic patterns of the VMs, and compare those patterns with the company's current network security group (NSG) settings. From there, Security Center can make recommendations about whether the NSGs should be locked down further and provide remediation steps.
- File integrity monitoring configure the monitoring of changes to important files on both Windows and Linux, registry settings, applications, and other aspects that might indicate a security attack.
Detect and respond to security threats by using Azure Sentinel
security information and event management (SIEM)
Azure Sentinel is Microsoft's cloud-based SIEM system. It uses intelligent security analytics and threat analysis.
Azure Sentinel capabilities:- collect+Investigate+detect+respond
- Collect cloud data at scale Collect data both on-premises and from multiple clouds.
- Investigate threats with artificial intelligence Examine suspicious activities at scale, tapping into years of cybersecurity experience from Microsoft.
- Detect previously undetected threats Minimize false positives by using Microsoft's comprehensive analytics and threat intelligence.
- Respond to incidents rapidly Use built-in orchestration and automation of common tasks.
Store and manage secrets by using Azure Key Vault
Azure Key Vault is a centralized cloud service for storing an application's secrets in a single,central location.
What are the benefits of Azure Key Vault?
The benefits of using Key Vault include:
- Centralized application secrets
- Securely stored secrets and keys Azure uses industry-standard algorithms, key lengths, and HSMs. Access to Key Vault requires proper authentication and authorization.
- monitor and control access to your application secrets
- Simplified administration of application secrets Key Vault makes it easier to enroll and renew certificates from public certificate authorities (CAs). You can also scale up and replicate content within regions and use standard certificate management tools.
- Integration with other Azure services
Azure Dedicated Host:
- Gives you visibility into, and control over, the server infrastructure that's running your Azure VMs.
- Helps address compliance requirements by deploying your workloads on an isolated server.
- Lets you choose the number of processors, server capabilities, VM series, and VM sizes within the same host.
You're charged per dedicated host, independent of how many VMs you deploy to it. The host price is based on the VM family, type (hardware size), and region.
Software licensing, storage, and network usage are billed separately from the host and VMs.
Layers of defense in depth :
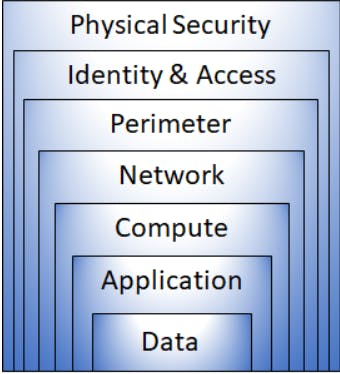
- The physical security layer-protect computing hardware in the datacenter.
- The identity and access layer controls access to infrastructure and change control.
- The perimeter layer uses distributed denial of service (DDoS) protection to filter large-scale attacks before they can cause a denial of service for users.
- The network layer limits communication between resources through segmentation and access controls.
- The compute layer secures access to virtual machines.
- The application layer helps ensure that applications are secure and free of security vulnerabilities.
- The data layer controls access to business and customer data that you need to protect.
Security posture
Your security posture is your organization's ability to protect from and respond to security threats. CIA.
Confidentiality
The principle of least privilege means restricting access to information only to individuals explicitly granted access
Integrity : - Prevent unauthorized changes to information:
Availability
Ensure that services are functioning and can be accessed only by authorized users. Denial-of-service attacks are designed to degrade the availability of a system, affecting its users.
What's Azure Firewall?
Protect virtual networks by using Azure Firewall
Azure Firewall is a stateful firewall
Azure Firewall provides many features, including:
- Built-in high availability.
- Unrestricted cloud scalability.
- Inbound and outbound filtering rules.
- Inbound Destination Network Address Translation (DNAT) support.
- Azure Monitor logging.
Azure Firewall, you can configure:
- Application rules that define fully qualified domain names (FQDNs) that can be accessed from a subnet.
- Network rules that define source address, protocol, destination port, and destination address.
- Network Address Translation (NAT) rules that define destination IP addresses and ports to translate inbound requests.
DDoS Protection- Basic and standard service layer available
- Volumetric attacks
- Protocol attacks
Resource-layer (application-layer) attacks (only with web application firewall)
What are network security groups?
A network security group enables you to filter network traffic to and from Azure resources within an Azure virtual network.
Compare authentication and authorization
- Authentication is the process of establishing the identity of a person or service that wants to access a resource. It establishes whether the user is who they say they are.
- Authentication establishes the user's identity, but authorization is the process of establishing what level of access an authenticated person or service has.It specifies what data they're allowed to access and what they can do with it.
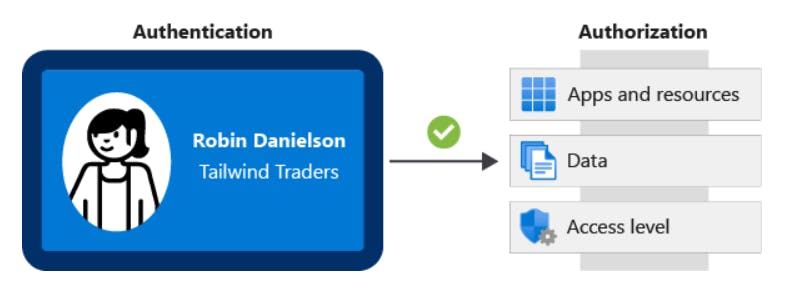
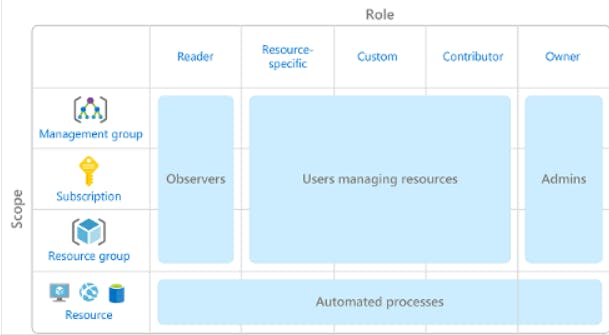
Azure Role-Based Access Control :- Azure RBAC
- When you assign the Owner role to a user at the management group scope, that user can manage everything in all subscriptions within the management group.
- When you assign the Reader role to a group at the subscription scope, the members of that group can view every resource group and resource within the subscription.
- When you assign the Contributor role to an application at the resource group scope, the application can manage resources of all types within that resource group
RBAC uses an allow model. When you're assigned a role, RBAC allows you to perform certain actions, such as read, write, or delete. If one role assignment grants you read permissions to a resource group and a different role assignment grants you write permissions to the same resource group, you have both read and write permissions on that resource group.
Plan and manage your Azure costs
Total Cost of Ownership Calculator= TCO
- Define your workloads: Server, database, storage, networking
- Adjust assumptions : Electricity,IT administration,Network maintenance cost
- View the report.
What types of Azure subscriptions can I use?
Free trial
A free trial subscription provides you with 12 months of popular free services, a credit to explore any Azure service for 30 days, and more than 25 services that are always free.
Pay-as-you-go
A pay-as-you-go subscription enables you to pay for what you use by attaching a credit or debit card to your account. Organizations can apply for volume discounts and prepaid invoicing.
Member offers
Your existing membership to certain Microsoft products and services might provide you with credits for your Azure account and reduced rates on Azure services.
How do I purchase Azure services?
- Through an Enterprise Agreement
- Directly from the web
- Through a Cloud Solution Provider
What factors affect cost?
- Resource type
- Usage meters
- Resource usage
- Azure subscription types
- Azure Marketplace
- Location
- Zones for billing of network traffic
